How to cover tracks over Network :
Covering Tracks Using Reverse HTTP Shells :
In this type of attack, the attacker installs a reverse HTTP shell on the victim computer. This reverse HTTP shell is coded is such a way that it ask the commands from an external moderator who controls this reverse shell at regular intervals. So it looks like a normal traffic to an organization network perimeter security device like a firewall, as port 80 is usually opened.
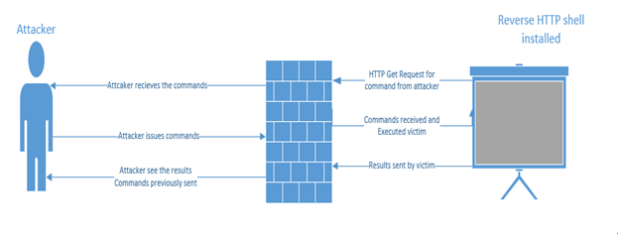
Once the attacker receives the request from the reverse HTTP shell, commands will be issued back that will be executed locally by the victim. This all is seen as HTTP request /response to the network devices. Once the commands get executed, results will be sent out in the next web request. These HTTP reverse shells can also be programmed to bypass any static authentication required by perimeter devices, like a firewall.
Covering Tracks using ICMP Tunnels :
Because HTTP reverse shells are so famous, some organizations keep a check on what is leaving their network in response to the client’s GET request. Some also check what comes as a reply to a GET request and most probably the attacker commands can be detected there. In lieu of this, some carry traffic via covert channels using ICMP packets. This is usually successful because organizations block only incoming ICMP packets and forgot about outgoing ICMP packets. Because of this configuration, an attacker uses ICMP packets to transfer TCP payloads.

First the attacker configures the local client to connect with the victim client. The victim in turn encapsulates the TCP payload in an ICMP ECHO packet and forwards it to the proxy server. The proxy server in turn de-encapsulates the packet and extracts the TCP payload and send to attacker. To the network devices, it seems like a simple ICMP packet.
Various tools are available to do this. Some of them are given below:
- Ptunnel
- Loki
- ICMPShell
- PingChat
- ICMPCmd
_357c1652_ using TCP Parameters :
How about distributing the attacker’s payload via the normal TCP packet instead of the encapsulating protocol? This method is well known and even today can be used to bypass IDS/IPS. The attacker can distribute the payload via the unset parameters of the TCP packet.
Some of the interesting fields in TCP packet that can be used to transfer the content are:
- IP Identification: This attack is very simple to conduct. It requires an established session between the two sides. From one side the payload is transferred bitwise in the IPID field.
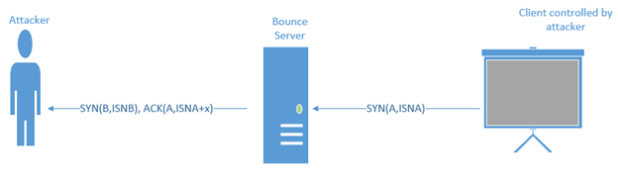
- TCP initial acknowledgement sequence number: This is a tricky method. This method uses a bounce server whose whole purpose is to receives the packet from the client and send it to the attacker machine. Below are the steps that are used in this method
- Client generates a TCP SYN packet with a spoofed source address of the receiving server and destination address of the bounce server. Let’s say the initial sequence number is ISNA, which holds the character to be transmitted.
- Bounce server receives the packet and responds SYN-ACK OR RESET, based on whether the port is closed or not. An interesting point is that it does send a reply, but to where? Yes, it sends the reply to the receiving server because it receives a spoofed source address. It replies with a SYNB, ACK(ISNA+1).
- Receiving server receives this and recovers the character from sequence number field.
- TCP initial sequence number: This method does not even require am established connection as is required in the IP identification method. A SYN packet is sent with an ISNa (initial sequence number) containing the payload (bit). Even though if it gets a RESET in reply, the content is already been extracted by the other side.

0 Comments:
Post a Comment