2. Enter your bitcoin address on From address
3. Enter opponent bitcoin address at To field
4. Enter amount of BTC and click next step
5. Transaction fee for every transaction is 0.0001 BTC


This is slide 1 description. Go to Edit HTML of your blogger blog. Find these sentences. You can replace these sentences with your own words. This is a Blogger template by NewBloggerThemes.com...

This is slide 2 description. Go to Edit HTML of your blogger blog. Find these sentences. You can replace these sentences with your own words. This is a Blogger template by NewBloggerThemes.com...

This is slide 3 description. Go to Edit HTML of your blogger blog. Find these sentences. You can replace these sentences with your own words. This is a Blogger template by NewBloggerThemes.com...

This is slide 4 description. Go to Edit HTML of your blogger blog. Find these sentences. You can replace these sentences with your own words. This is a Blogger template by NewBloggerThemes.com...

This is slide 5 description. Go to Edit HTML of your blogger blog. Find these sentences. You can replace these sentences with your own words. This is a Blogger template by NewBloggerThemes.com...

















Why Linux only?
Setting up
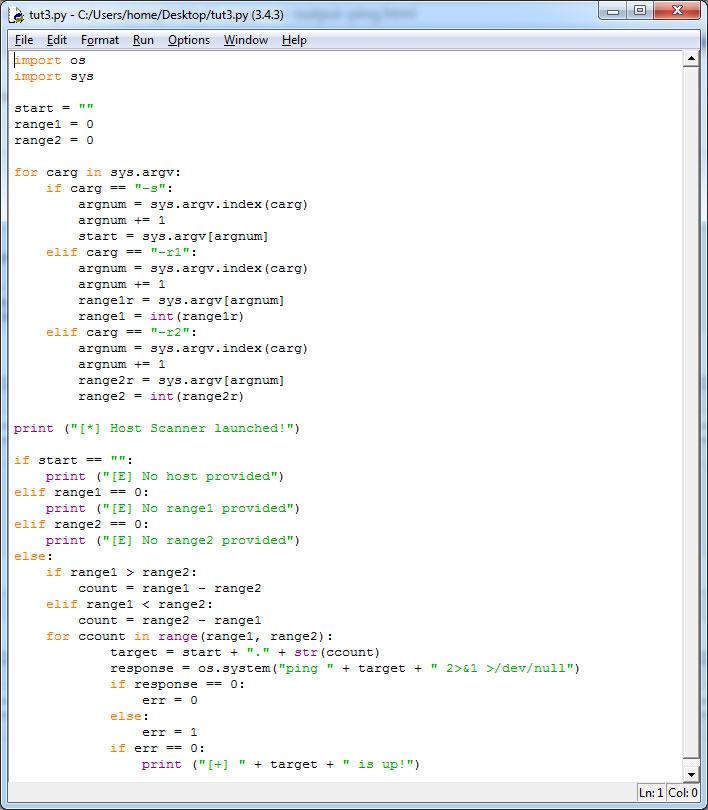
import os # Importing main libsimport sysstart = "" # Setting up variablesrange1 = 0range2 = 0
for carg in sys.argv: # Checking for argumentsif carg == "-s":argnum = sys.argv.index(carg)argnum += 1start = sys.argv[argnum]elif carg == "-r1":argnum = sys.argv.index(carg)argnum += 1range1r = sys.argv[argnum]range1 = int(range1r)elif carg == "-r2":argnum = sys.argv.index(carg)argnum += 1range2r = sys.argv[argnum]range2 = int(range2r)
print ("[*] Host Scanner launched!") # Informs user about initialize
if start == "": # Checks if all the information is providedprint ("[E] No host provided")elif range1 == 0:print ("[E] No range1 provided")elif range2 == 0:print ("[E] No range2 provided")else:if range1 > range2:count = range1 - range2elif range1 < range2:count = range2 - range1for ccount in range(range1, range2): # Counts the IP range to pingtarget = start + "." + str(ccount)response = os.system("ping " + target + " 2>&1 >/dev/null") # Sets response to pingif response == 0: # Reads response, checks if it is 0err = 0 # sets err to 0else:err = 1 # sets err to 1if err == 0: # when err is equal to 0print ("[+] " + target + " is up!") # Informs user about hosts that are up
Code should look like this (comments are cut, do not worry):
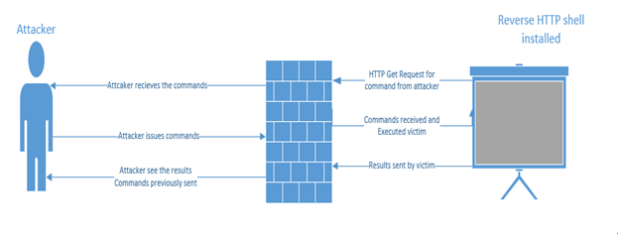
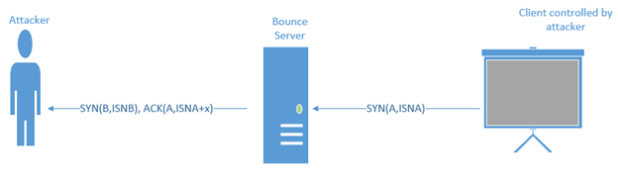
 Now with all good stories there are two sides. With the advantages that I have described, there are disadvantages. Now while I could myself describe what these are, I felt that a fellow member by the name of Charles Kane did it better than I could have with his scenario given. Please read this quote given and all credit goes to him for this part:
Now with all good stories there are two sides. With the advantages that I have described, there are disadvantages. Now while I could myself describe what these are, I felt that a fellow member by the name of Charles Kane did it better than I could have with his scenario given. Please read this quote given and all credit goes to him for this part:1. Open the Control Panel.
2. Open up Network and Internet and go to the Network and Sharing Center.
3. Click on Change adapter settings on the left hand panel.
4. This will bring up a list of adapters present on your computer. Most people will have a Local Area Connection while laptop users will add a Wireless Network Connection and possibly a Bluetooth Network Connection...go ahead andright click on Local Area Connection and click on Properties.
NOTE: These steps do not change if you are modifying the Wireless Network Connection instead
5. If prompted by UAC, click on Yes.
6. Highlight Internet Protocol Version 4 (TCP/IPv4) and click on properties.
7. In the properties window you will see a few radio boxes with both of them saying Obtain an IP/DNS Address Automatically....we will leave the IP address alone and will change the Obtain DNS....to use the following:In the Preferred DNS server boxes enter this sequence: 208.67.222.222
In the Alternate DNS server boxes enter this sequence: 208.67.220.220
8. Check the validate settings upon exit (Optional) check box, click OK, and then Close to finish. (See screenshot above)
9. Windows will check your settings (if you checked the option above) and you will be finished! Now start surfing to feel the effects of a quicker and more secure browsing experience!

Depends entirely on what you are looking for, here are some:
"favorite links" Keyword(s)
"favorite links"
"favorite sites" Keyword(s)
"favorite sites"
"Keyword(s) sites"
"Keyword(s) website"
"Keyword(s)"
"list * Keyword(s) * sites"
"list * Keyword(s)"
"list of Keyword(s) sites"
"list of Keyword(s)"
"recommended links" Keyword(s)
"recommended links"
"recommended sites" Keyword(s)
"recommended sites"
directory * Keyword(s)
intitle:directory "Keyword(s)"
inurl:directory "Keyword(s)"
Keyword(s)
Keyword(s) * directory
Keyword(s) catalog
Keyword(s) directory
Keyword(s) sites
Keyword(s) websites |Keyword(s)
Keyword(s) websites
Designers will become more like programmers as programming becomes more like design.
BETA Version of SiGploit will have the Location Tracking attacks of the SS7 phase 1
1) Python 2.7
2) Java version 1.7 +
python bin/SiGploit.py




1 | sudo add–apt–repository ppa:kilian/f.lux |
1 | sudo apt–get update |
1 | sudo apt–get install fluxgui |
You want to force people coming to your site to use HTTPS. Either for the entire site or a small sub-section of it.
Note
Using mod_rewrite to do this isn't the recommended behavior.
RewriteEngine On
# This will enable the Rewrite capabilities
RewriteCond %{HTTPS} !=on
# This checks to make sure the connection is not already HTTPS
RewriteRule ^/?(.*) https://%{SERVER_NAME}/$1 [R,L]
# This rule will redirect users from their original location, to the same location but using HTTPS.
# i.e. http://www.example.com/foo/ to https://www.example.com/foo/
# The leading slash is made optional so that this will work either in httpd.conf
# or .htaccess context
Entire site (.htaccess) :
Note: While the rules you need are the same as above (because the rule above doesn't depend on any of the quirks of rewrite in .htaccess), you will need to ensure that you place this in a .htaccess file in the root of the site you want to apply it against, and to make sure you have the appropriate AllowOverride configuration in your httpd.conf
Specific Directory
Either put the above solution in a .htaccess file in the directory to be affected, or put the URI prefix in the regex itself.
RewriteEngine On
# This will enable the Rewrite capabilities
RewriteCond %{HTTPS} !=on
# This checks to make sure the connection is not already HTTPS
RewriteRule ^/?secure/(.*) https://%{SERVER_NAME}/secure/$1 [R,L]
# This rule will redirect all users who are using any part of /secure/ to the same location but using HTTPS.
# i.e. http://www.example.com/secure/ to https://www.example.com/secure/
# This means if you dont want to force HTTPS for all directories you can force it for a specific sub-section of the site.
| Kali Linux commands | Function |
|---|---|
| A | |
| apropos | Search Help manual pages (man -k) |
| apt-get | Search for and install software packages (Debian) |
| aptitude | Search for and install software packages (Debian) |
| aspell | Spell Checker |
| awk | Find and Replace text, database sort/validate/index |
| B | |
| basename | Strip directory and suffix from filenames |
| bash | GNU Bourne-Again Shell |
| bc | Arbitrary precision calculator language |
| bg | Send to background |
| break | Exit from a loop |
| builtin | Run a shell builtin |
| bzip2 | Compress or decompress named files |
| C | |
| cal | Display a calendar |
| case | Conditionally perform a command |
| cat | Concatenate and print (display) the content of files |
| cd | Change Directory |
| cfdisk | Partition table manipulator for Linux |
| chgrp | Change group ownership |
| chmod | Change access permissions |
| chown | Change file owner and group |
| chroot | Run a command with a different root directory |
| chkconfig | System services (runlevel) |
| cksum | Print CRC checksum and byte counts |
| clear | Clear terminal screen |
| cmp | Compare two files |
| comm | Compare two sorted files line by line |
| command | Run a command – ignoring shell functions |
| continue | Resume the next iteration of a loop |
| cp | Copy one or more files to another location |
| cron | Daemon to execute scheduled commands |
| crontab | Schedule a command to run at a later time |
| csplit | Split a file into context-determined pieces |
| cut | Divide a file into several parts |
| D | |
| date | Display or change the date and time |
| dc | Desk Calculator |
| dd | Convert and copy a file, write disk headers, boot records |
| ddrescue | Data recovery tool |
| declare | Declare variables and give them attributes |
| df | Display free disk space |
| diff | Display the differences between two files |
| diff3 | Show differences among three files |
| dig | DNS lookup |
| dir | Briefly list directory contents |
| dircolors | Colour setup for `ls’ |
| dirname | Convert a full pathname to just a path |
| dirs | Display list of remembered directories |
| dmesg | Print kernel & driver messages |
| du | Estimate file space usage |
| E | |
| echo | Display message on screen |
| egrep | Search files for lines that match an extended expression |
| eject | Eject removable media |
| enable | Enable and disable builtin shell commands |
| env | Environment variables |
| ethtool | Ethernet card settings |
| eval | Evaluate several commands/arguments |
| exec | Execute a command |
| exit | Exit the shell |
| expect | Automate arbitrary applications accessed over a terminal |
| expand | Convert tabs to spaces |
| export | Set an environment variable |
| expr | Evaluate expressions |
| F | |
| false | Do nothing, unsuccessfully |
| fdformat | Low-level format a floppy disk |
| fdisk | Partition table manipulator for Linux |
| fg | Send job to foreground |
| fgrep | Search files for lines that match a fixed string |
| file | Determine file type |
| find | Search for files that meet a desired criteria |
| fmt | Reformat paragraph text |
| fold | Wrap text to fit a specified width |
| for | Expand words, and execute commands |
| format | Format disks or tapes |
| free | Display memory usage |
| fsck | File system consistency check and repair |
| ftp | File Transfer Protocol |
| function | Define Function Macros |
| fuser | Identify/kill the process that is accessing a file |
| G | |
| gawk | Find and Replace text within files |
| getopts | Parse positional parameters |
| grep | Search files for lines that match a given pattern |
| groupadd | Add a user security group |
| groupdel | Delete a group |
| groupmod | Modify a group |
| groups | Print group names a user is in |
| gzip | Compress or decompress named files |
| H | |
| hash | Remember the full pathname of a name argument |
| head | Output the first part of files |
| help | Display help for a built-in command |
| history | Command History |
| hostname | Print or set system name |
| I | |
| iconv | Convert the character set of a file |
| id | Print user and group id’s |
| if | Conditionally perform a command |
| ifconfig | Configure a network interface |
| ifdown | Stop a network interface |
| ifup | Start a network interface up |
| import | Capture an X server screen and save the image to file |
| install | Copy files and set attributes |
| J | |
| jobs | List active jobs |
| join | Join lines on a common field |
| K | |
| kill | Stop a process from running |
| killall | Kill processes by name |
| L | |
| less | Display output one screen at a time |
| let | Perform arithmetic on shell variables |
| ln | Create a symbolic link to a file |
| local | Create variables |
| locate | Find files |
| logname | Print current login name |
| logout | Exit a login shell |
| look | Display lines beginning with a given string |
| lpc | Line printer control program |
| lpr | Off line print |
| lprint | Print a file |
| lprintd | Abort a print job |
| lprintq | List the print queue |
| lprm | Remove jobs from the print queue |
| ls | List information about files |
| lsof | List open files |
| M | |
| make | Recompile a group of programs |
| man | Help manual |
| mkdir | Create new folders |
| mkfifo | Make FIFOs (named pipes) |
| mkisofs | Create an hybrid ISO9660/JOLIET/HFS filesystem |
| mknod | Make block or character special files |
| more | Display output one screen at a time |
| mount | Mount a file system |
| mtools | Manipulate MS-DOS files |
| mtr | Network diagnostics (traceroute/ping) |
| mv | Move or rename files or directories |
| mmv | Mass Move and rename files |
| N | |
| netstat | Networking information |
| nice | Set the priority of a command or job |
| nl | Number lines and write files |
| nohup | Run a command immune to hangups |
| notify-send | Send desktop notifications |
| nslookup | Query Internet name servers interactively |
| O | |
| open | Open a file in its default application |
| op | Operator access |
| P | |
| passwd | Modify a user password |
| paste | Merge lines of files |
| pathchk | Check file name portability |
| ping | Test a network connection |
| pkill | Stop processes from running |
| popd | Restore the previous value of the current directory |
| pr | Prepare files for printing |
| printcap | Printer capability database |
| printenv | Print environment variables |
| printf | Format and print data |
| ps | Process status |
| pushd | Save and then change the current directory |
| pwd | Print Working Directory |
| Q | |
| quota | Display disk usage and limits |
| quotacheck | Scan a file system for disk usage |
| quotactl | Set disk quotas |
| R | |
| ram | ram disk device |
| rcp | Copy files between two machines |
| read | Read a line from standard input |
| readarray | Read from stdin into an array variable |
| readonly | Mark variables/functions as readonly |
| reboot | Reboot the system |
| rename | Rename files |
| renice | Alter priority of running processes |
| remsync | Synchronize remote files via email |
| return | Exit a shell function |
| rev | Reverse lines of a file |
| rm | Remove files |
| rmdir | Remove folders |
| rsync | Remote file copy (Synchronize file trees) |
| S | |
| screen | Multiplex terminal, run remote shells via ssh |
| scp | Secure copy (remote file copy) |
| sdiff | Merge two files interactively |
| sed | Stream Editor |
| select | Accept keyboard input |
| seq | Print numeric sequences |
| set | Manipulate shell variables and functions |
| sftp | Secure File Transfer Program |
| shift | Shift positional parameters |
| shopt | Shell Options |
| shutdown | Shutdown or restart linux |
| sleep | Delay for a specified time |
| slocate | Find files |
| sort | Sort text files |
| source | Run commands from a file |
| split | Split a file into fixed-size pieces |
| ssh | Secure Shell client (remote login program) |
| strace | Trace system calls and signals |
| su | Substitute user identity |
| sudo | Execute a command as another user |
| sum | Print a checksum for a file |
| suspend | Suspend execution of this shell |
| symlink | Make a new name for a file |
| sync | Synchronize data on disk with memory |
| T | |
| tail | Output the last part of file |
| tar | Tape Archiver |
| tee | Redirect output to multiple files |
| test | Evaluate a conditional expression |
| time | Measure Program running time |
| times | User and system times |
| touch | Change file timestamps |
| top | List processes running on the system |
| traceroute | Trace Route to Host |
| trap | Run a command when a signal is set(bourne) |
| tr | Translate, squeeze, and/or delete characters |
| true | Do nothing, successfully |
| tsort | Topological sort |
| tty | Print filename of terminal on stdin |
| type | Describe a command |
| U | |
| ulimit | Limit user resources |
| umask | Users file creation mask |
| umount | Unmount a device |
| unalias | Remove an alias |
| uname | Print system information |
| unexpand | Convert spaces to tabs |
| uniq | Uniquify files |
| units | Convert units from one scale to another |
| unset | Remove variable or function names |
| unshar | Unpack shell archive scripts |
| until | Execute commands (until error) |
| uptime | Show uptime |
| useradd | Create new user account |
| usermod | Modify user account |
| users | List users currently logged in |
| uuencode | Encode a binary file |
| uudecode | Decode a file created by uuencode |
| V | |
| v | Verbosely list directory contents (`ls -l -b’) |
| vdir | Verbosely list directory contents (`ls -l -b’) |
| vi | Text Editor |
| vmstat | Report virtual memory statistics |
| W | |
| wait | Wait for a process to complete |
| watch | Execute/display a program periodically |
| wc | Print byte, word, and line counts |
| whereis | Search the user’s $path, man pages and source files for a program |
| which | Search the user’s $path for a program file |
| while | Execute commands |
| who | Print all usernames currently logged in |
| whoami | Print the current user id and name (`id -un’) |
| wget | Retrieve web pages or files via HTTP, HTTPS or FTP |
| write | Send a message to another user |
| X | |
| xargs | Execute utility, passing constructed argument lists |
| xdg-open | Open a file or URL in the user’s preferred application |
| Y | |
| yes | Print a string until interrupted |
